Machine Programming Vulnerabilities
#lecture note based on 15-213 Introduction to Computer Systems
H2 Attacks by overwriting memory
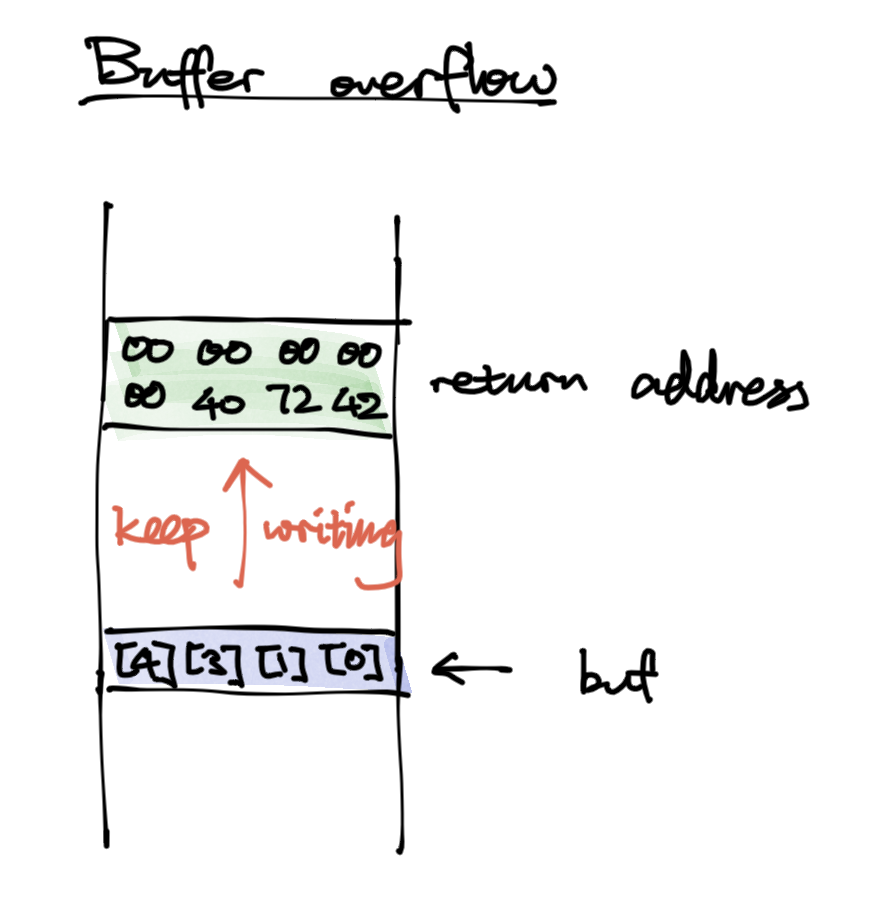
buffer overflow / stack smashing attack - big cause of security vulnerability. If going beyond array range we could write things to unknown places.
One could overwrite the return address and have rip jump somewhere to execute what they want.
Things that could be unsafe
strcpygets
H2 Some protection strategies
- Avoid overflow vulnerability
fgetsstrncpyscanfwith%nswherenis integer
- System level protection
- randomised stack offset, so that attacker don’t know where to jump to
- add random bytes onto stack when program starts
- shift entire stack
- non-executable memory
- added an additional bit to specify execute permission, so seg fault if jumping into stack
- randomised stack offset, so that attacker don’t know where to jump to
- Stack canaries (compiler’s job) - pretty good defence
- compiler allocates special (random) value called “canary” on stack beyond buffer if it sees buffer-ish stuff in the code. Check for corruption before returning. This is the
%fs:0x28thing in bomb lab.
- compiler allocates special (random) value called “canary” on stack beyond buffer if it sees buffer-ish stuff in the code. Check for corruption before returning. This is the
H2 More attacking (other strategies)
Alternative strategy: Using existing code - the C library (we know where the C library is, and it’s executable)
Look for ret viz. 0xc3, then the thing before it we can make use of to do what we want.
We can also jump into the middle of instructions in the C library.
If we can start overwriting return addresses on the stack, we can point them to the small instructions in the C library. Putting these pieces together we can do more complex things.
Note this doesn’t work with code compiled with canary unless some other exploit exposes the canary.